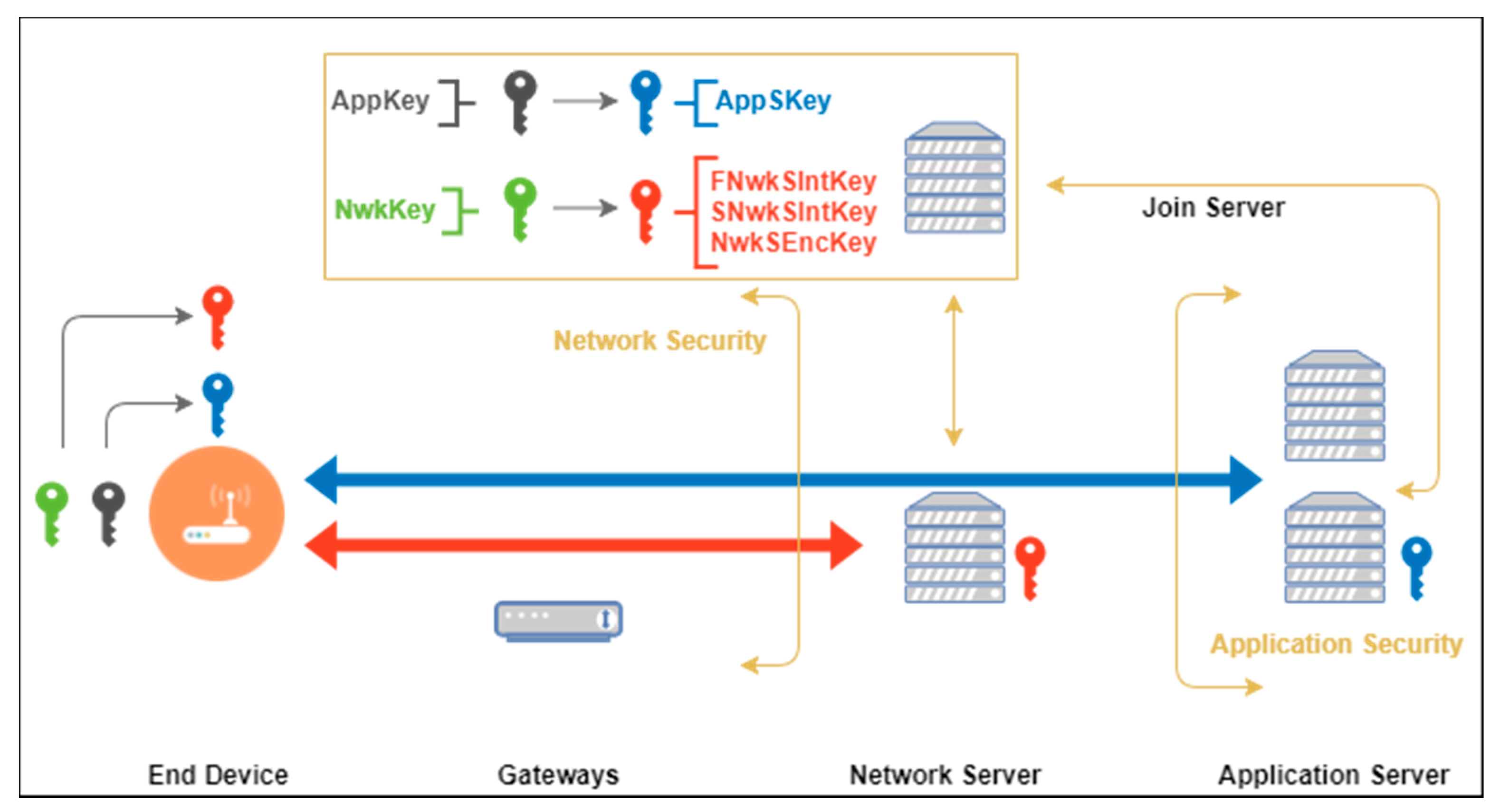
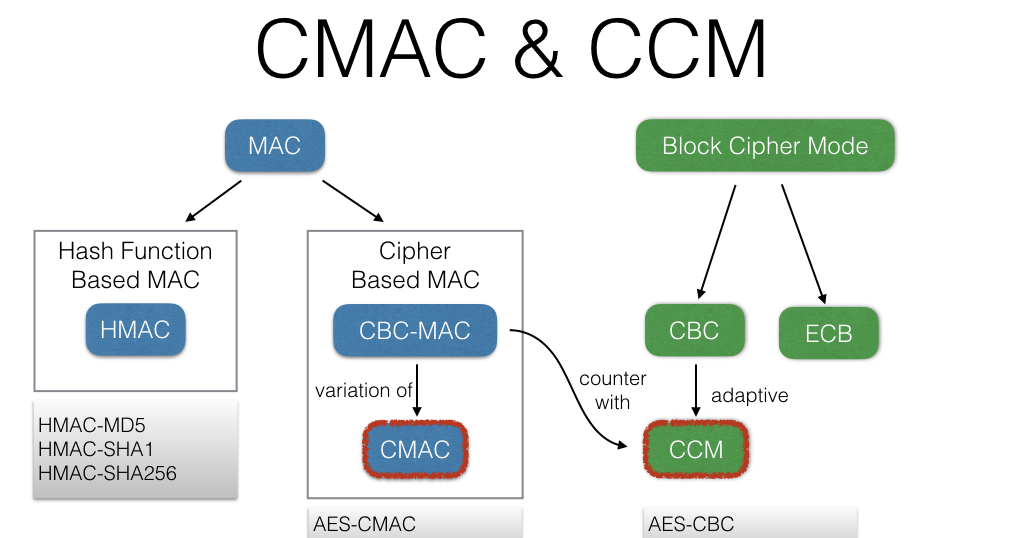
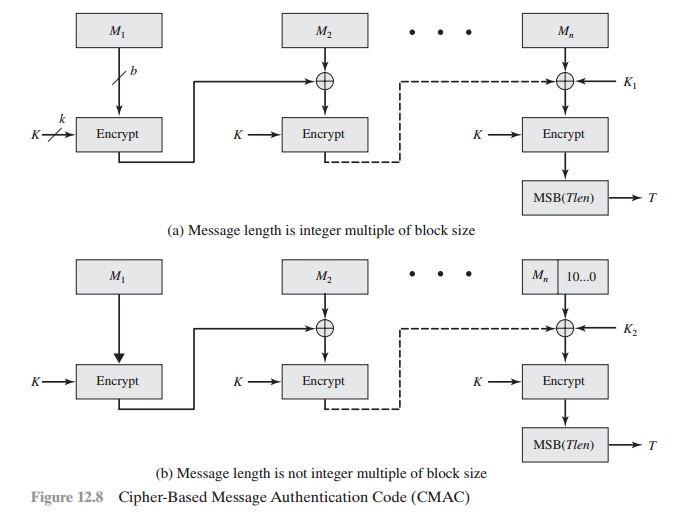
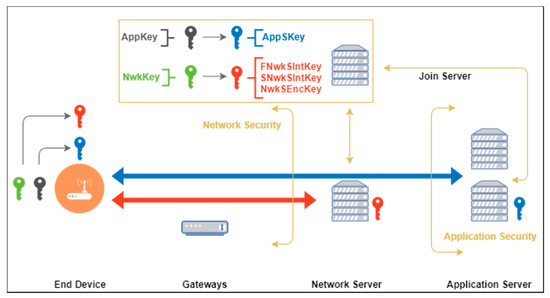
Sensors | Free Full-Text | A Key Management Protocol Based on the Hash Chain Key Generation for Securing LoRaWAN Networks
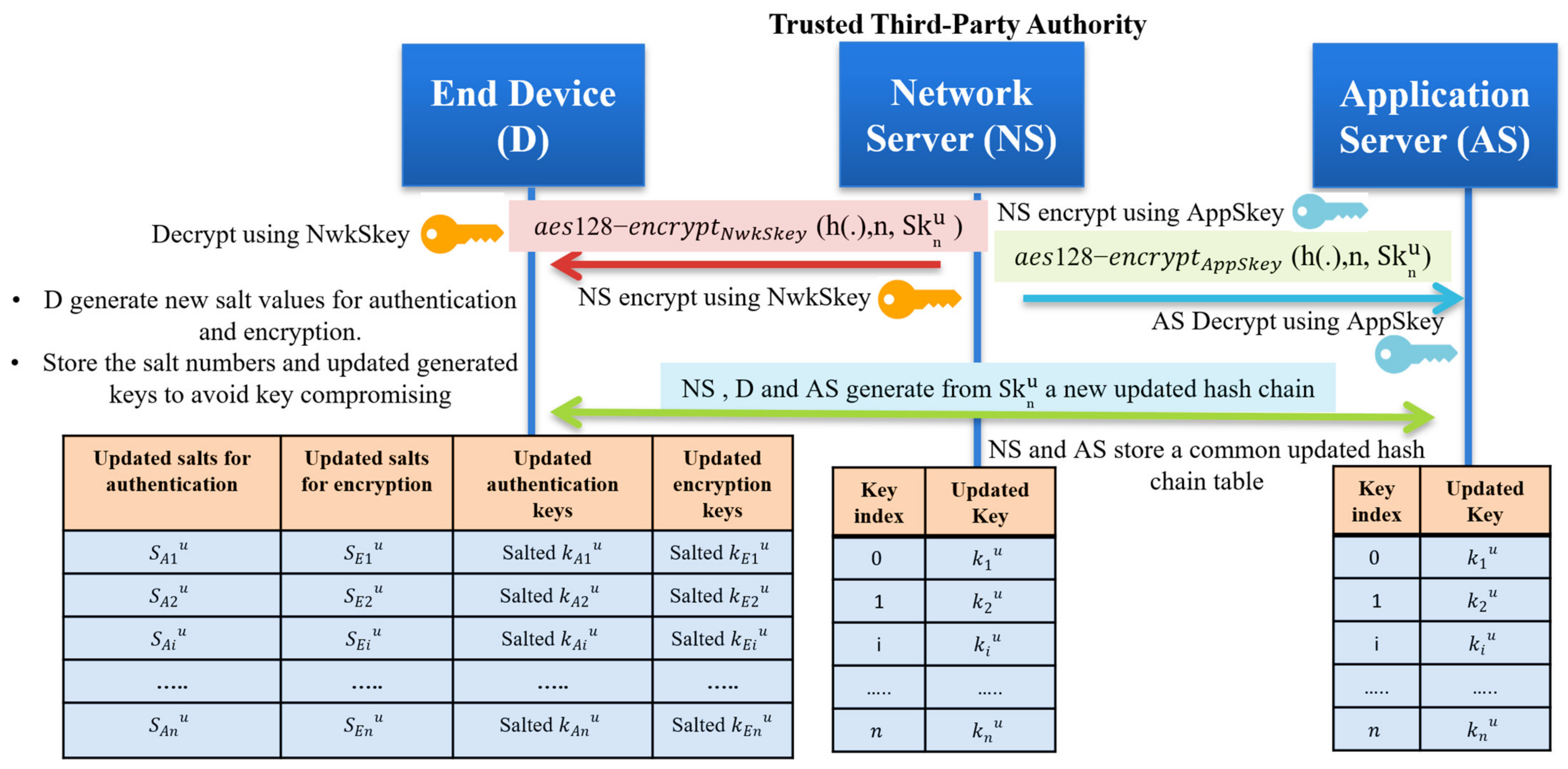
Sensors | Free Full-Text | A Key Management Protocol Based on the Hash Chain Key Generation for Securing LoRaWAN Networks
GitHub - artjomb/cryptojs-extension: Extensions for CryptoJS containing AES- CMAC, AES-SIV and AES-EAX implementations



![Research needed] Handling .cmd CMACs on SD card · Issue #340 · d0k3/GodMode9 · GitHub Research needed] Handling .cmd CMACs on SD card · Issue #340 · d0k3/GodMode9 · GitHub](https://user-images.githubusercontent.com/35666439/55248846-0737b300-5221-11e9-9aad-858f69b2663e.png)