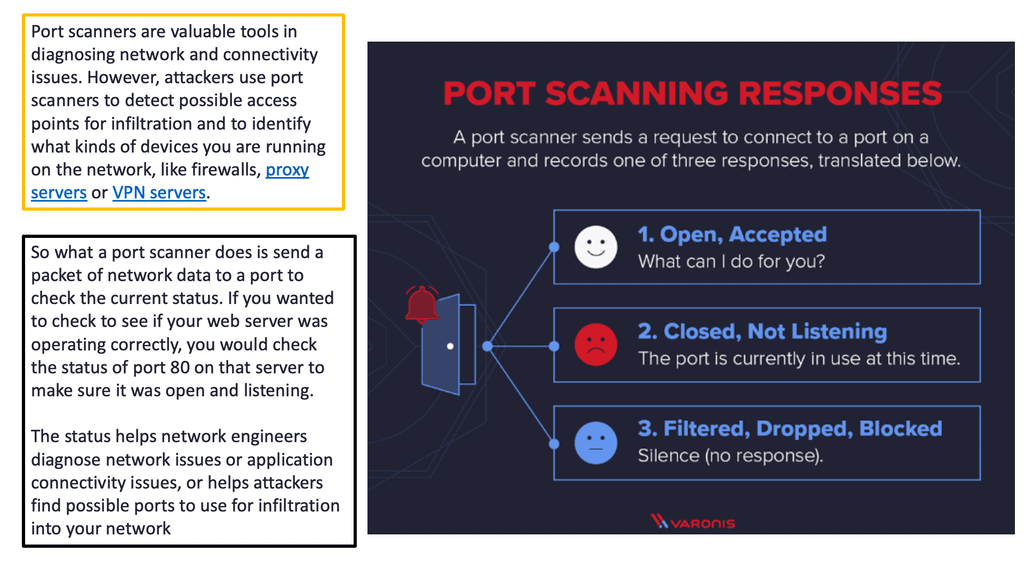
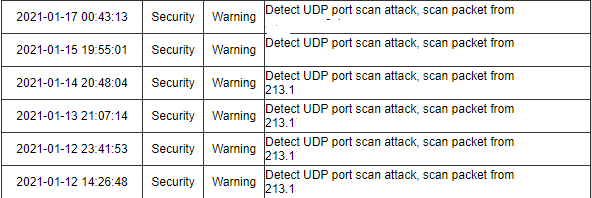
Attack Defense - AR100, AR120, AR150, AR160, AR200, AR1200, AR2200, AR3200, and AR3600 V200R010 CLI-based Configuration Guide - Security - Huawei

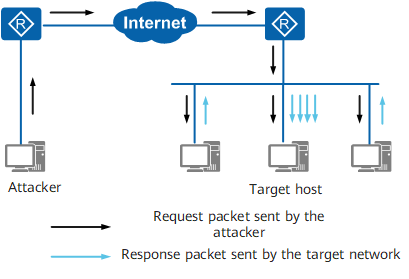
UDP scan attack comparison. Full-size DOI: 10.7717/peerj-cs.787/fig-6 | Download Scientific Diagram



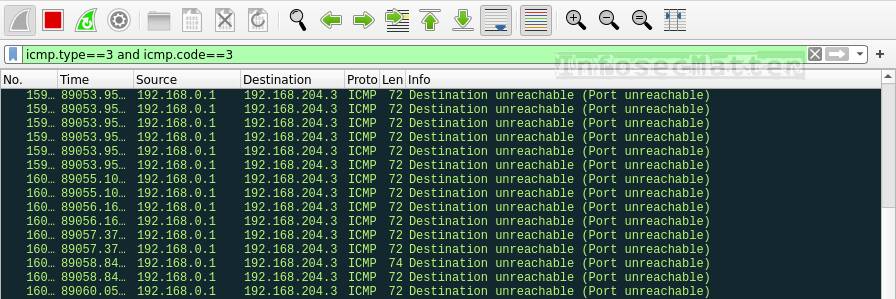
![KB2951] Resolve "Detected Port Scanning Attack" notifications (15.x–16.x) KB2951] Resolve "Detected Port Scanning Attack" notifications (15.x–16.x)](https://support.eset.com/storage/IMAGES/en/KB2951/KB2951Fig1-1e.png)

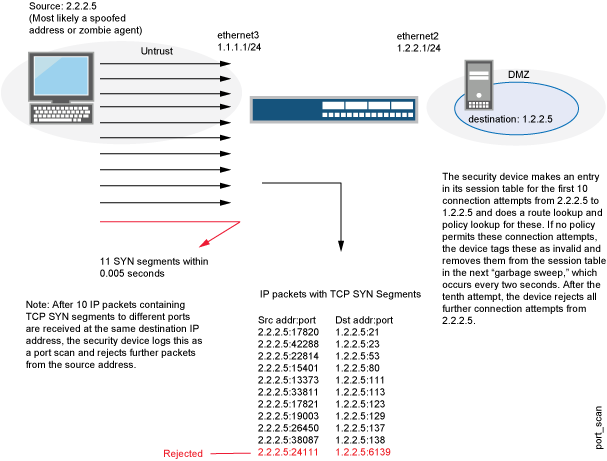


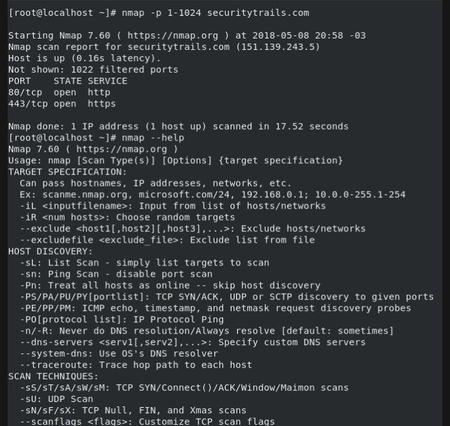
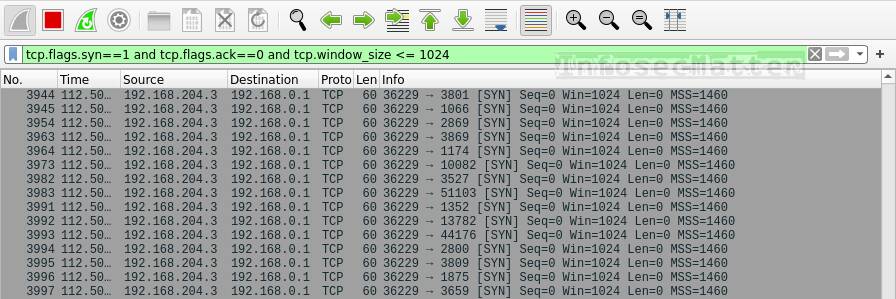
![PDF] Detection and Characterization of Port Scan Attacks | Semantic Scholar PDF] Detection and Characterization of Port Scan Attacks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/8830f1780bd7da10fd6090346b83d17fc9b09c97/5-Table1-1.png)